Get a quick preview of Edgescan’s comprehensive security platform.
Validated results. Zero false positives. No noise.
We deliver what we promise.
See what our clients have to say about us.
How Edgescan supports your CTEM program
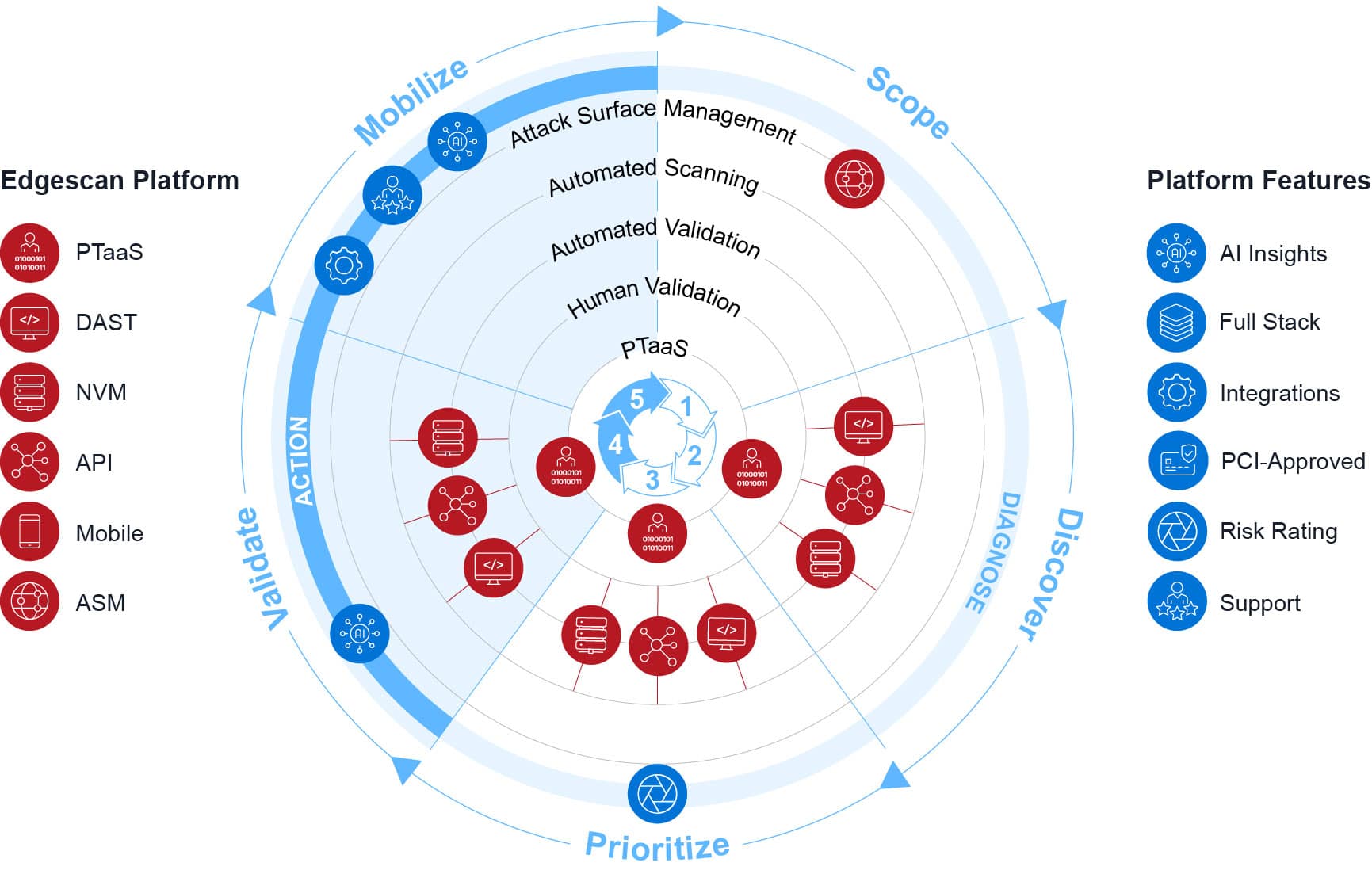
The Edgescan Platform
Continuous security testing and exposure management
Edgescan’s continuous testing platform strengthens your CTEM program with 100% false-positive-free, validated vulnerability intelligence so you can quickly find and fix risks.
Penetration Testing as a Service (PTaaS)
Dynamic Application Security Testing (DAST)
Recognizing the gaps in automated vulnerability scanning alone, we added human + AI layers to our service. This ensured our clients received accurate vulnerability risk, minimizing false positives and helping customers prioritize fixes with proven exploits. AI can be enabled to assist with vulnerability clarity, breach probability, prioritization and improve overall context.
Network Vulnerability Management (NVM)
API Security Testing
Mobile Application Security Testing (MAST)
The explosion of mobile devices in enterprise environments meant security couldn’t be neglected. Edgescan now includes comprehensive mobile application security testing to address the unique threats that mobile apps often present.
Attack Surface Management (ASM)

Award-Winning Services
Contact us for more information on how Edgescan can help secure your business.




