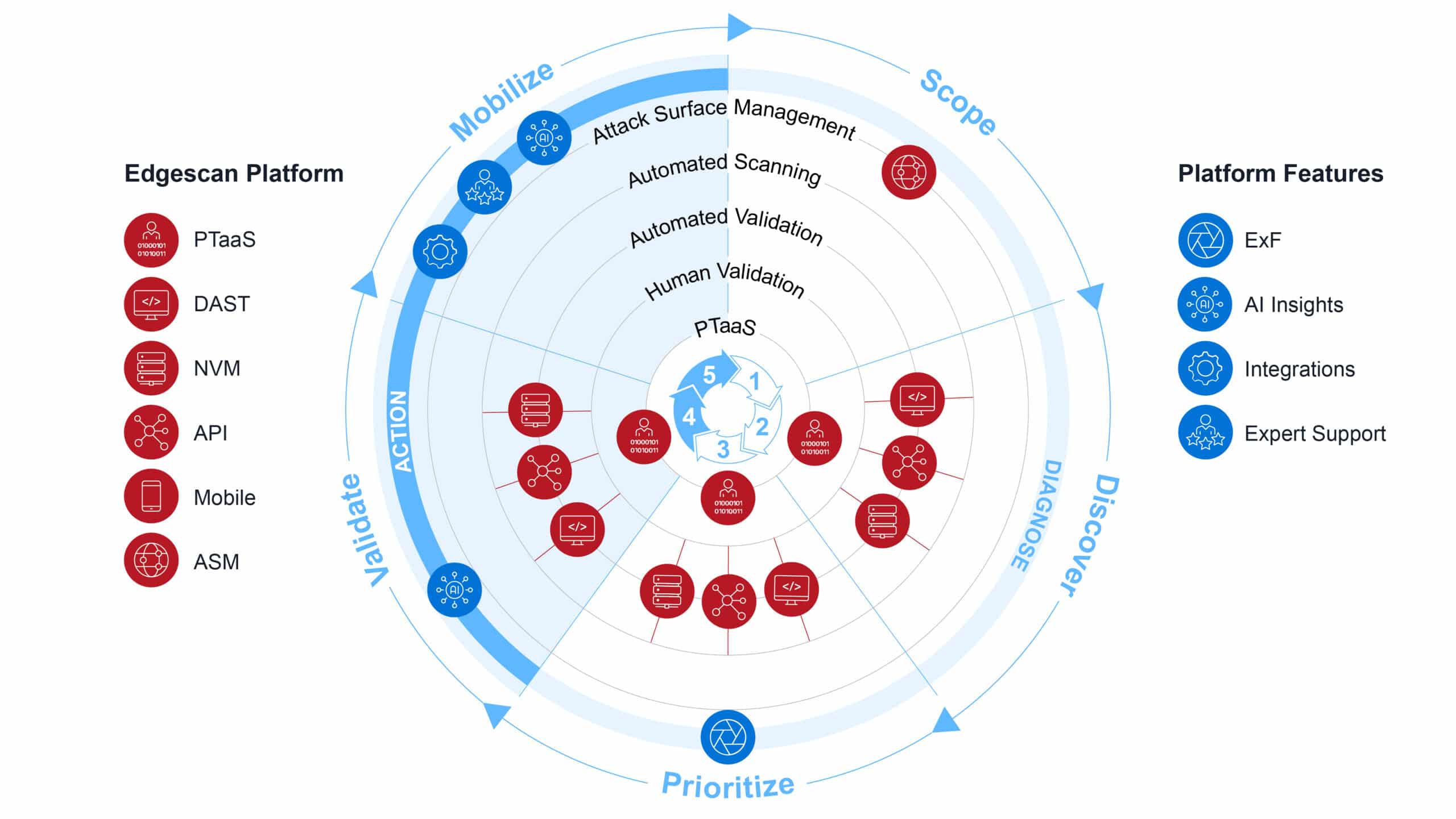
When you look at Edgescan as a platform, we’ve been delivering CTEM for many, many years—before Gartner coined the phrase in 2022.
What is CTEM/TEM?
Deliver Scope for Cybersecurity Exposure: Investigate an organization’s “Attack Surface”—vulnerable entry points and exposures—and discover assets.
Improve Security Posture: By continuously monitoring, assessing, prioritizing, and resolving security issues, CTEM helps organizations improve their security posture and efficiently use an organization’s resources.
Prioritize Threats: The goal of any robust TEM process is not to fix every single security issue discovered. Everyone has a vulnerability backlog, and we need to fix what has a decent probability of a breach.
Validate how a successful exploit might work: Confirm/Validate whether an attacker could actually exploit a vulnerability and what the impact might be. Provide a working example that explains the issue to non-cyber team members and executives.
The above is not rocket science, and I question if this actually deems an acronym TBH… 🙂
Edgescan’s Evolution (CTEM before CTEM was a “thing”)
Vulnerability Detection:
We started with RBVM (Risk Based Vulnerability Management) in 2016, which consisted of automated DAST and device security scanning combined with cyber analytics and expert human validation for high and critical severity vulnerabilities. We have tested hundreds of thousands of assets to date with this SaaS, delivering validated vulnerability data, saving our clients time and money.
In 2020, we started using our Data Lake of 15,000,000 vulnerability data signatures. Given it was all validated manually, the accuracy lent well to an analytics model, which is used to verify the probability a discovered vulnerability is real – An additional level of validation to help ensure accuracy.
In 2021, we deployed a Single-Page Application (SPA) scanning feature to parse JavaScript and dynamic HRefs, which many scanners miss. We also deployed API scanning technology, which consumes API descriptors to cover the API endpoints’ attack surface properly.
In 2022, we deployed dynamic mapping to CISA KEV and EPSS to provide additional ways to prioritize vulnerabilities. In 2023, we delivered EXF (Edgescan eXposure Factor), combining traditional severity ratings like OWASP and CVSS with EPSS and CISA KEV to provide even more actionable insight into what to prioritize.
Attack Surface Management:
2017: We deployed “Continuous Asset Profiling,” Now called ASM (Attack Surface Management), coined by Gartner in 2021. This evolved from continuous profiling of named IP ranges for exposures, services, and ports to EASM (External ASM), which crawls the internet, discovers IPs, API’s subdomains, certificate health, defensive HTTP headers, and brute forcing to name a few features…more here: https://www.edgescan.com/asm-done-right/
Penetration Testing (as a Service): PTaaS
In 2018, we deployed “Edgescan Advanced” to provide depth of testing. It was designed to discover vulnerabilities that automation has difficulty with by combining both automation and human expertise. We currently have one of Europe’s largest penetration testing teams, delivering this service at a massive scale. The mantra was “Automate the shite out of everything as long as accuracy and coverage do not suffer”. This has worked, and Edgescan delivers (as of last month, April 2024) 160+ penetration tests every month via the platform. Testing is CREST Pentest compliant using a team of OSCP, CEH experts. We deliver this globally, combined with the above ASM and RBVM on-demand via the Edgescan platform.
Situational Awareness & Integrations:
Alerting, Events & SOAR (Security Orchestration, Automation and Response) is a solution stack of compatible software programs that allow an organization to collect data about security threats from multiple sources and respond to low-level security events without human involvement and in real-time.
Edgescan enables SOAR in many ways:
- Vulnerability Discovery/Closure/Event Alerting
- EASM/ASM Asset Event Alerting
- API Discovery
- Internal mitigation SLA alerts (vulnerability age alerts).
- And much more: https://www.edgescan.com/integrations/
Once a vulnerability is discovered, it undergoes validation and risk rating to help ensure it is accurate and detailed enough to guide DevSecOps/Admin staff to mitigate the risk. “Edgescan Events” provide alerting to named members of staff or dedicated channels.
Artificial Intelligence:
We can’t talk about our Black Ops’ development team and what they are working on. But be assured, its very, very cool and will provide real value to our clients (as opposed to us).
Conclusion
So regarding CTEM/TEM, yes, Edgescan is and has been a CTEM solution (with ASM) even before analysts coined the phrase. I thought it was best to point this out in a “room full of many loud voices.”