It is that time of the year again when Verizon Business release its world-renowned Data Breach Incidence Report (DBiR).
As per previous years, it discussed the avenues for breach and has some commentary on trends within the industry.
For the fourth year in a row, Edgescan was invited to submit data to the research, and we did. We shared thousands of validated vulnerabilities based on the previous 12 months of delivering Penetration Testing as a Service and Risk-Based Vulnerability Management assessments to over 250 organizations globally across multiple verticals.
Looking at the 2024 report some key points resonate:
25-year-old vulnerabilities are still a serious problem
The report cited a substantial growth of attacks involving the exploitation of vulnerabilities as the critical path to initiate a breach compared to previous years. They increased by 180% from last year due to widespread vulnerabilities such as MOVEit and similar zero-day vulnerabilities.
The MOVEit vulnerability (CVE-2023-34362) affected at least 122 organizations and exposed the data of roughly 15 million people. It was, in effect, a SQL injection attack. It’s worth remembering that SQL Injection (SLQI) was discovered in 1998. So, we are still dealing with 25-year-old vulnerabilities, which does not bode well for the cybersecurity and development industry.
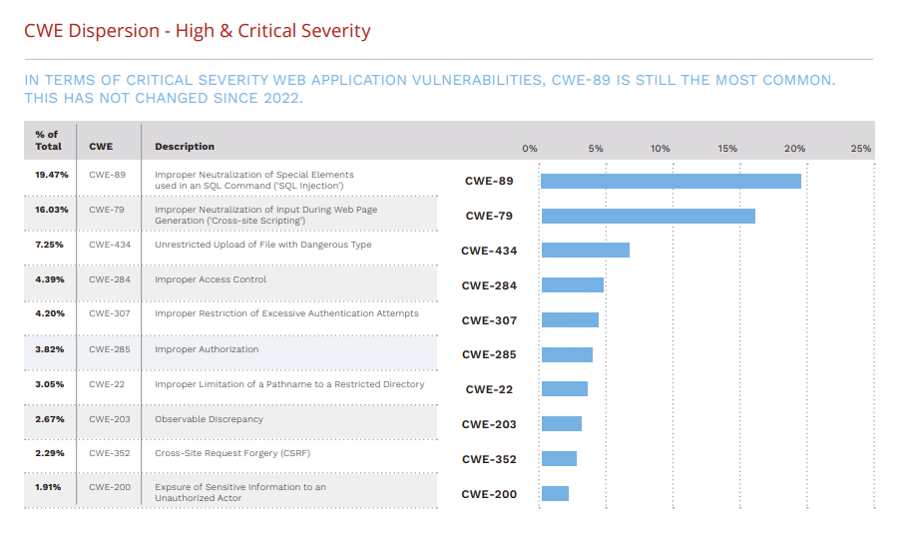
SQLI was also the most common critical severity vulnerability discovered by Edgescan, per the 2024 Edgescan Vulnerability Statistics Report.
One must consider with all the new approaches to application & cloud security: CTEM, BAS, ETM, CRQ, ASPM, CCA, IAST, TBPT, CAASM, CWAP etc, not forgetting AI based coding and assessment solutions, the dial has not moved very much. I believe the industry is moving “ahead” while ignoring the problem.
Once breached, such attacks were primarily leveraged by Ransomware and other Extortion-related threat actors. As one might imagine, Web applications were the main vector for those initial entry points.
So we need to think about two things here:
- Web applications (and software in general) weakness is the avenue for attack for Ransomware and extortion actors. Ensuring systems are secure makes this job harder for the attacker. A SQLI injection can not only be used to “dump” databases but also be used as a foothold for a Ransomware attack.
- The initial vector may well be phishing, credential stealing, or credential-based attacks, but once in, pivoting is made much easier via unpatched CVE’s and software vulnerabilities.
Artificial General Intelligence (AGI) threat landscape is nonexistent
To paraphrase the report:
The folks in Verizon concluded that “after performing text analysis of criminal forums data contributors, we could obviously see the interest in GenAI (as in any other forum, really), but the number of mentions of GenAI terms alongside traditional attack types and vectors such as “phishing,” “malware,” “vulnerability” and “ransomware” were extremely low, circa 100 cumulative mentions over the past two years.” – One would assume that cybercriminals are ahead of the curve in terms of techniques and approached to exploit & breach. Obviously, we are not there yet regarding the threat of “Evil AI”, but I’m sure the day will come.
The top “Action Vectors” in breaches are Web Applications
The report cites stolen credentials as a significant avenue of attack. Given that credentials are used with web applications, they go hand in hand with the use of stolen credentials and the exploitation of vulnerabilities to infiltrate defences.
MTTR – Fixing code and Patching
The report discusses “survival analysis of CISA KEV vulnerabilities.” It refers to CISA and claims to have found that it takes around 55 days to remediate 50% of critical vulnerabilities once their patches are available. Patching and mitigation generally do not occur in force until after the 30-day mark, and 12 months later, around 8% of CISA KEV vulnerabilities are still open.
At Edgescan, we find delivering both CISA KEV and EPSS metadata is important in terms of prioritization. In my opinion, the days of CVSS-based priority are numbered. In summary, the DBiR states “if its in the KEV fix ASAP.”
Web applications a favorite for Ransomware
In terms of “ways-in,” web applications are second to “direct Install” attacks, which leverage existing backdoors. This is followed by email attacks. Ransomware accounts for a large 11% of all incidents across 92% of industry verticals, which gives rise to the value of web application security. The DBiR team predicts that we will continue to see zero-day vulnerabilities being widely leveraged by ransomware groups into the future. Think MOVEit or Log4Shell.
Basic web application attacks
“Threat actors continue to take advantage of assets with default, simplistic and easily guessable credentials via brute forcing them, buying them or reusing them from previous breaches.” When discussing an assessment, it is recommended that the scope of testing include such techniques. 100% of attacks against web applications were from an external source. User credentials were the most common “trophy” from a Web Application attack. 13% of breaches involved exploiting a vulnerability in a web application. “The Financial and Insurance (18%); Information (14%); and Professional, Scientific and Technical Services (13%) industries make up the top three verticals affected by Basic Web Application Attacks.”
Conclusion:
Poor authentication mechanisms and weak passwords are very common vectors of a successful breach. Consider a strong password policy and multifactor authentication controls.
Web application security is an underrated asset when it comes to defense against Ransomware.
CISA KEV is a key indicator of what needs to be fixed ASAP. Old vulnerabilities still produce the most “bang for the buck.”
AGI (Artificial General Intelligence) is not a clear and present danger yet!! But its day will come. Focus on the basics.