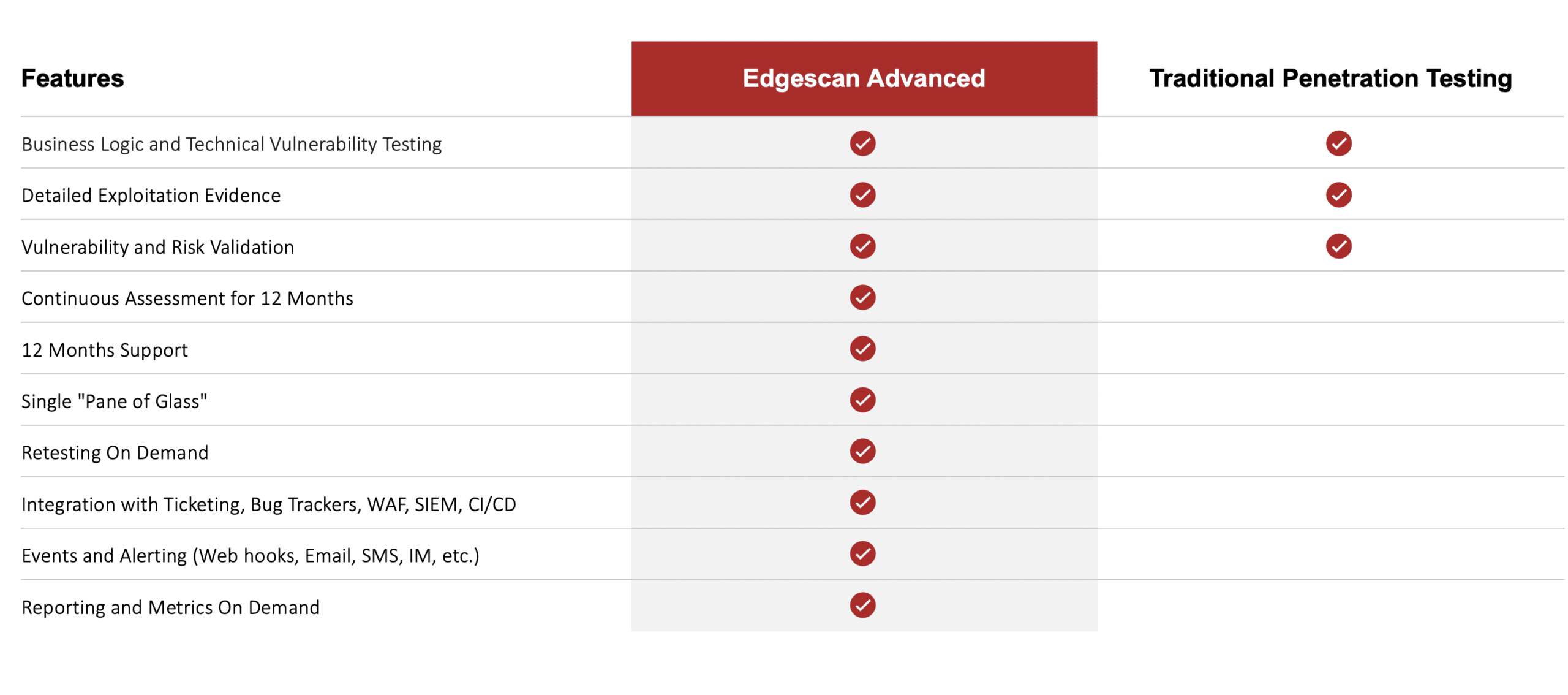
In my role at Edgescan, I often come across teams with 1 to 5 InfoSec professionals. These teams typically include a mix of security-minded, development-focused, and administrative roles, with a leader spearheading their efforts. While each team and organization is different, one factor remains the same across each program: Everyone is trying to do as much as they can with the people and budget that they are allocated. With that in mind, I’ve listed the five most common ways that Edgescan impacts these teams that feel the pain of tight budgets and resource scarcity.
5 Ways Edgescan Helps Small Security Teams Succeed
1 Getting Onboard: No Tool Configuration or Maintenance Required
With Edgescan, the work of configuring and maintaining scanners isn’t put on you and your team. Simply tell us what you need tested, and we’ll handle the setup. Our asset blocker workflow even alerts you to issues (such as DNS resolution) preventing thorough scanning. If we’re scanning on your internal or private network, we’ll build a virtual machine for you, all you need to do is deploy it.
2 Getting Real Vulnerability Data: Hybrid Vulnerability Triage
I think we’re all in agreement that no one likes false-positives and false-negatives. Our hybrid approach to validation uses AI, analytics, and human expertise to validate vulnerabilities efficiently. We auto-validate low-hanging fruit and have pen testers manually review high/critical vulns to weed out false positives and negatives. For your team, this means you can spend more time making critical remediations and less time working through the noise that scanners produce.
3 Context and Narrative: Simplifying Prioritization with Key Metrics and Factors
Edgescan provides 5 ; levers for prioritization, including EVSS (Edgescan Validated Security Score), CVSS, EPSS (Exploit Prediction Scoring System, by FirstOrg) , CISA KEV and EXF (Edgescan Exposure Factor, aggregated risk score to ensure that each remediation has a tangible impact on overall risk across all regulatory bodies). We provide all of these levers to help you prioritize remediations. Beyond scoring systems, each vulnerability that Edgescan presents provides detail around the impact of the vulnerability, should a hacker utilize this attack path. This is all part of an effort to help you easily determine which fixes will have the greatest impact for your organization and eliminate risk across any applicable framework.
4 Simplifying Fixes: Step-by-Step Remediation Guidance
For each vulnerability, Edgescan spells out any and all methods to remediate or patch the vulnerability identified. If there’s a simple fix, such as “update to version X,” we’ll include the links so your team doesn’t have to scour the web. We’ll also provide any associated CVEs, CWEs, and/or CIS Control Violations. No more guessing how to fix issues or wondering if you’ve closed gaps. We give you a clear roadmap.
5 Help From Experts: Expert-Led Support for Everybody
If you ever have a question or just want some advice, every Edgescan client, regardless of package, has access to our in-house team of Crest and OSCP certified pen testers. Each and every one of our clients, regardless of size or spend, get the answers and expertise necessary to understand the impact of vulnerabilities and remediations made.
In Conclusion: Do More With the Resources You Have
We understand, more than most, the time and effort that tools create. We also understand how hard it is to get a pentest done and then hope that your remediations take effect before the next assessment. Nobody likes being surprised come audit time! Edgescan was created by pen testers to solve the problems they experienced when they were in the thick of it, just like you and your teams – we take care of all of the work leading up to remediation, so you can do more with less. Get more for your security with your existing budget, by partnering with Edgescan.
Contact us to learn more about simplifying security for your team.