Mobile Application Security Testing (MAST)
Vulnerability Assessment + Penetration Testing + Device Forensics
Comprehensive mobile application security testing that addresses the unique threats that mobile apps often present.
As organizations increasingly provide mobile applications to enable their remote workforce and boost productivity, their security teams must ensure the safety and integrity of these mobile devices, apps and data. With the rapid and expanding use of mobile apps in the workforce, comes an extended attack surface for cybercriminals to potentially access.
Mobile risk assessments discover and examine all assets within your mobile devices and applications to expose vulnerabilities and threats that may jeopardize data security or performance. MAST includes a device forensics component, unique to the mobile attack surface. It is designed to detect leakage of data onto a device or jailbroken associated risks.
Make mobile
apps safe
The mobile application threat landscape is increasingly complex and dynamic, posing substantial risks to both individuals and organizations. As enterprise mobile app usage increases, it is essential to implement a robust security testing program and stay informed about evolving threats to safeguard sensitive information.
Ensure your applications and devices remain secure. Our continuous security testing, and device forensics solution gives you complete coverage across your mobile application ecosystem.
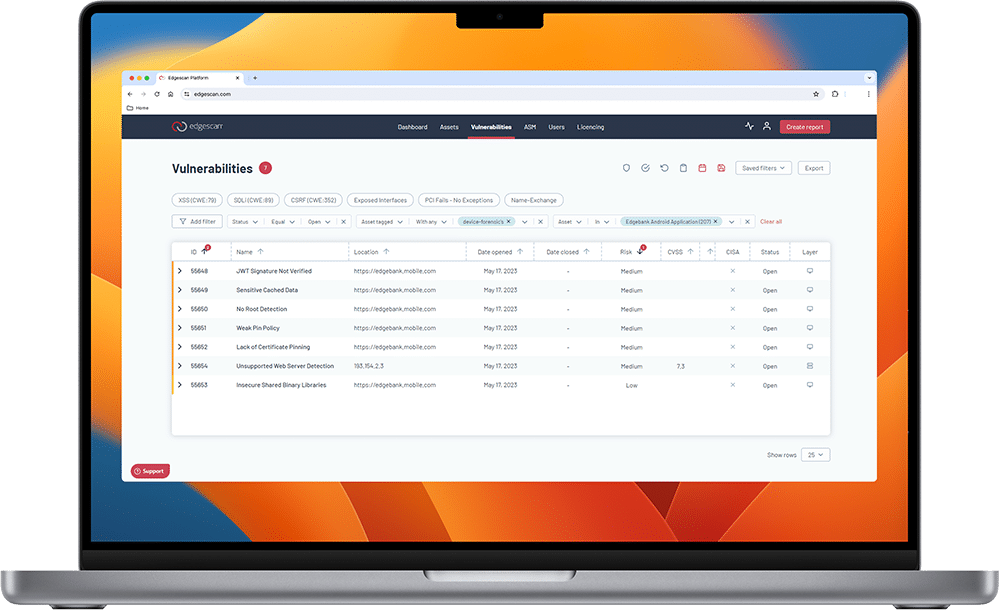
A single pane of glass view
1. Edgescan starts with ingesting the API components used by mobile devices and applications into its platform.
2. Then our vulnerability scanning engine builds a precise profile of each application and runs an assessment of it and at the host-server layer.
3. After the initial scan is completed, a manual penetration test is performed against the API/App, to test for business logic vulnerabilities and vulnerabilities that legacy scanners cannot find.
4. Edgescan then downloads a build of the native mobile application onto our test devices and begins deep testing and device forensics.
5. All results are provided to the Edgescan platform allowing for unlimited retesting and reporting, while ensuring data is safely stored, transmitted, and secured in your mobile environment.
1. Edgescan starts with ingesting the API components used by mobile devices and applications into its platform.
2. Then our vulnerability scanning engine builds a precise profile of each application and runs an assessment of it and at the host-server layer.
3. After the initial scan is completed, a manual penetration test is performed against the API/App, to test for business logic vulnerabilities and vulnerabilities that legacy scanners cannot find.
4. Edgescan then downloads a build of the native mobile application onto our test devices and begins deep testing and device forensics.
5. All results are provided to the Edgescan platform allowing for unlimited retesting and reporting, while ensuring data is safely stored, transmitted, and secured in your mobile environment.
Mobile apps have at least one critical vulnerability
In a recent study by Check Point Research in 2023, approximately 75% of mobile applications have at least one critical vulnerability.
Mobile applications with at least one critical vulnerability
Benefits of using Mobile Application Testing
Full stack security
Prioritized,
actionable results
Customizable reporting
Certified experts
Meet compliance
Edgescan is a certified PCI ASV and delivers testing covering the OWASP Top 10, WASC threat classification, CWE/SANS Top 25.
Full stack security
Prioritized,
actionable results
Customizable reporting
Certified experts
Meet compliance
Edgescan is a certified PCI ASV and delivers testing covering the OWASP Top 10, WASC threat classification, CWE/SANS Top 25.
Edgescan Mobile Application Security Testing (MAST) is a software as a service, sold as an annual subscription.
For more information on how Edgescan can help secure your business, contact: sales@edgescan.com
IT SECURITY MANAGER
NETWORK ADMINISTRATOR
CYBERSECURITY ANALYST
IT MANAGER
SECURITY OPERATIONS LEAD
CHIEF INFORMATION SECURITY OFFICER