Penetration Testing as a Service (PTaaS)
Human Experts + Automation + Analytics
On-demand penetration testing with unlimited retests, expert remediation guidance, proven exploits, validated risk, streamlined reports, and unlimited vulnerability assessments
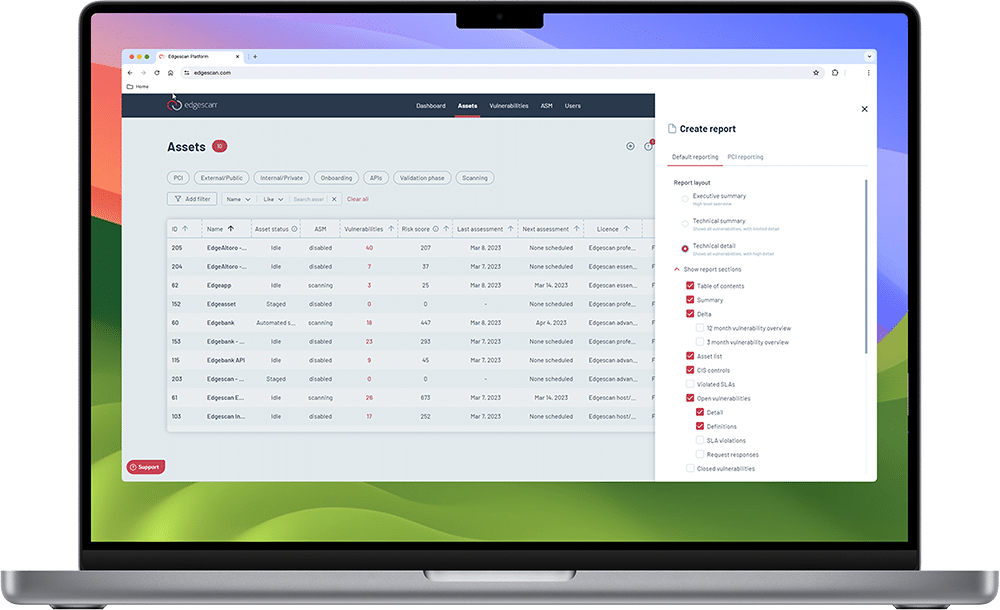
Our penetration testing as a service (PTaaS) is a hybrid solution that combines the breadth of automation with the depth of human assessment, while integrated with advanced vulnerability management and cyber analytics. The pen testing platform includes in-depth validated vulnerability assessments, automatically validates risk, and then rates that risk against a suite of risk databases. Penetration testing as a service (PTaaS) can be used to assess web applications, APIs and network/cloud devices.
We provide real and actionable results
How it works
The Edgescan suite of solutions is utilized during pen tests. The scanning engine speeds up and assists with reconnaissance and discovery, allowing Edgescan to scale continuous testing without sacrificing accuracy.
1. During an assessment, the Edgescan validation engine queries millions of vulnerability examples stored in our data lake.
2. Vulnerability data is then run through our proprietary analytics models to determine if the vulnerability is a true positive.
3. If it meets a certain numeric threshold it is released to the customer; we call this an auto-commit vulnerability.
4. If the confidence level falls below the threshold or the vulnerability is of critical or high severity, then the vulnerability is flagged for expert validation by an Edgescan security analyst.
Organizations lack the skills to conduct penetration tests
67% of organizations say they do not have the necessary skills to conduct thorough penetration tests. This statistic is drawn from the Ponemon Institute’s report on the state of penetration testing, emphasizing a critical gap in expertise within organizations.
Organizations Lacking the Skills to Pen Test
Benefits of using a PTaaS testing solution
Certified Experts
Edgescan is a CREST certified organization, combining years of experience with top industry accreditations to deliver industry-recognized foremost service.
Customizable reporting
Enables auditing and trend analysis by tracking closed vulnerabilities, vulnerability age, posture status, and many other security metrics. Also create API-based reporting for GRC integrations per asset. No more sifting through pages of data and clunky PDFs.
Premium support
Dedicated support from a certified pen testing team. AI Insights provides real-time tactical advice to assist in immediate security posture improvement.
Depth and breadth
of coverage
Includes Edgescan DAST, Edgescan DAST for APIs, and/or Network Vulnerability Management for underlying hosting infrastructure.
Edgescan Penetration Testing as a Service (PTaaS) is a software as a service, sold as an annual subscription.
Contact us for more information on how Edgescan can help secure your business.
Types of penetration testing
API PTaaS
Continuous assessment using a combination of both automated tooling and certified CREST/OSCP expertise, smart API specific security automation and human expertise. On-demand penetration testing coupled with continuous vulnerability assessment, exposure validation, risk rating and support.
Application PTaaS
Network/Device PTaaS
Continuous internal and external assessments of networks, hosts and devices, using a combination of both automated tooling and certified CREST/OSCP expertise. On-demand penetration testing coupled with continuous vulnerability assessment, exposure validation, risk rating and support. Authenticated and unauthenticated testing for complete coverage.
Penetration Testing as a Sevice FAQs
Cost-effectiveness factors are complex and depend on several factors including:
- Size of an organization
- Scope of the target testing area
- Complexity of the environment
- Methodology used in testing
- Retesting and remediation support
- Skill set possessed by the pen testing team
In many cases, Penetration Testing as a Service(PTaaS) is more cost-effective than conducting pen testing internally with existing resources. On average, pen testing as a service can reduce costs by as much as 30% – and countless hours for customers.
Penetration Testing as a Service Reduces Overhead and Costs by 30%
For large, established enterprises with appropriate staffing and significant industry expertise, utilizing PTaaS increases the cost-effectiveness, accuracy, and productivity of in-house testing. Organizations of all sizes benefit from:
- Reduced overhead of SecOps teams and full-time employees
- Service delivered by an experienced expert full-time team
- Accurate results validated by a team dedicated to vulnerability intelligence.
- Unbiased assessment from a third-party
- Extended knowledge and familiarity with new products and technologies
- Meet compliance regulations: HIPAA, PCI DSS, TIBER EU, CBEST, SOC 2, ISO 2700, etc.
- Faster time to discovery and remediation
- Unlimited, retesting
- Remediation support from certified experts
- Greater scale, agility, risk awareness, and organizational resilience
The additional knowledge and expertise provided by PTaaS complements that of most organizations’ IT security teams and helps maintain industry compliance. Providing real and actionable results based on risk-rated results with prioritized remediation expedites and optimizes the whole testing process. Furthermore, the cost of employing PTaaS vs. the cost and ramifications of a data breach due to an unknown security loophole not discovered by internal pen testers, is far more advantageous. PTaaS helps ensure better coverage, efficiency, and accuracy as it is delivered by a team dedicated to vulnerability detection 24x7x365.
The answers are “yes” and “yes”. Since penetration testing, or “pentesting”, is designed to find exploitable security vulnerabilities and unintentional data exposure, thereby, helping organizations manage risk, meet compliance mandates, and maintain safe business continuity, it should be conducted on a regular basis. New vulnerabilities and exploits are discovered weekly, if not daily, and, to discover and mitigate the critical ones, pentesting should be executed regularly.
So how often should your organization run pentests?
As there is no specific, mandatory time frame, it depends on the size and industry type of your organization, your available resources, and the scale of testing you want to conduct. Follow what is best for your organization’s overall security strategy and risk tolerance.
While there are many details involved in pentesting, the process can be described in several phases:
- Planning and reconnaissance – pentest goals are defined, and intelligence is gathered (e.g., email server, network and domain names),
- Scanning – tools are used to understand how a target responds to intrusions, typically using both static and dynamic analyses (e.g., SQL injections, brute force attacks),
- Gaining access – attacks are staged to discover the target’s vulnerabilities,
- Maintaining access – Advanced Persistent Threats (APTs) are imitated to verify if vulnerabilities can be used to maintain access,
- Analysis and device configuration – results are compiled into a report and then used to configure security device settings (e.g., WAFs, NGFW) before tests are run again.
The above process is conducted against externally accessible targets, such as the company’s website, email and domain name servers (DNS) to emulate an outside attacker, as well as against internal targets to imitate a malicious insider or disgruntled employee. Typically, a combination of automated tools and human-led testing and verification processes are used in any pentesting strategy.
The Edgescan PTaaS is a hybrid solution that combines the breadth of automation with the depth of human assessment, while integrated with advanced vulnerability management and analytics. PTaaS can be used to assess web applications, APIs and network/cloud devices utilizing risk rating methodologies to prioritize remediation. The platform employs several risk scoring systems (i.e., CVSS, CISA KEV, EPSS) and our own Edgescan Validated Security Score (EVSS) to risk-rate results.
The Edgescan PTaaS solution utilizes the Edgescan security team’s extensive technical expertise as well as the entire suite of applications within the Edgescan platform to provide vulnerability assessment, exposure validation, and risk ratings. Edgescan security experts offer battle-hardened security experience combined with countless industry accreditations such as CREST, OSCP, and CEH, to provide clients with deep wisdom and insight to readily resolve their security needs.
Penetration testing is where a security analyst simulates or investigates an IT (Information Technology) system (Web Application, Cloud, Network, API) with the aim to find any exploitable vulnerabilities. It is not uncommon to perform penetration tests on the application layer however it also extends into the network, cloud, IoT & API layers. The expected output of such an exercise is a report with detailed information discussing the method of discovery, Severity, Risk and associated remediation recommendations for the discovered vulnerabilities.
Examples of such discovered issues could include code-related weaknesses such as an OWASP Top 10 issue, a combination of host and web application weaknesses which result in a breach if combined, an authorization issue which could only be discovered by leveraging a logical weakness.
It’s labour intensive and expensive.
It does not scale very well.
It alone does not keep pace with the rapid pace of change.
It’s a point-in-time assessment in a changing world.
Traditional penetration testing does not keep pace with changes in your environment or the fact that new vulnerabilities are discovered every day. Today you may look secure, tomorrow a new vulnerability is known about, now you have a problem you did not have yesterday, without any of your systems changing!
Rapid: Retesting on demand to verify mitigation at no extra cost.
Efficient: Low administrative overhead and documentation required to deliver the penetration test.
Infinite: Continuous, validated assessment with on-demand deep expert-driven penetration testing.
Forecastable: Fixed license-based cost.
EASM: Continuous monitoring across your entire asset portfolio utilizing our External Attack Surface Management (EASM) solution
Event alerts: Alert integration into a variety of alerting and ticketing systems th
On-demand: On-demand reporting for any period of time per asset including assertation that the asset underwent a Penetration Test (PTaaS) by certified experts. API based reporting for GRC integration.
Reporting: Custom reporting including E.g;, closed vulnerabilities, vulnerability age, posture trending and other security metrics.
Break down silos of data: Integration of PTaaS output in the same repository as continuous vulnerability management output.
Remediation tracking: Internal Service Level Agreement (SLA) tracking, designed to help ensure high-severity vulnerabilities are mitigated in a timely manner.
Prioritization: CISA Exploit Catalogue mapping to help identify high-priority discovered vulnerabilities and aid prioritization. https://www.cisa.gov/known-exploited-vulnerabilities-catalog
Focused: Our security analysts are already familiar with the asset allowing for the human expertise to focus on complex and severe vulnerabilities whilst the technical vulnerabilities are discovered by Edgescan scanning technology.
Penetration Testing as a Service (PTaaS) is not automation, that’s scanning.
PTaaS is a hybrid solution that leverages human curiosity for depth and automation for breadth and analytics for verification and risk-based results.
PTaaS is a hybrid solution that combines the breadth of automation with the depth of human assessment, while integrated with advanced vulnerability management and analytics; it assesses for vulnerabilities which are not discovered by legacy scanning tools such as authorization or business logic. PTaaS can be used to assess web applications, APIs, cloud assets, and network devices utilizing risk rating methodologies to prioritize remediation.
With penetration test services results can be accessed in real-time instead of waiting for a report to be developed. When a discovered vulnerability is fixed, one can retest on-demand without engaging expensive consultants. Reporting is on demand also. Compare this to a traditional Penetration Test. If you performed a Penetration Test in May, you’d get your results in June and that’s it. Once you get your results you will no longer know if those vulnerabilities stay fixed or if new issues pop up.
Penetration testing as a service (PTaaS) offers greater scale, agility, and risk awareness versus traditional onsite pentesting tools and processes. Penetration testing as a service provides organizations of all sizes with the ability to expose and mitigate vulnerabilities without the need for significant human resources, saving time and costs, while maintaining compliance. This enables IT and SecOps teams to focus on enabling and securing their primary business objectives rather than overextending themselves into areas that are not their forte. By employing a penetration testing as a service, businesses can accelerate their development and operations, meet compliance mandates, as well as quickly and accurately discover and mitigate security vulnerabilities based on business risk without hindering the productivity of their organization. PTaaS solutions also provide metrics for education and preventative security.
Pentesting, whether deployed internally or delivered as a service, should be an integral component to any organization’s overall security strategy. Pentesting complements other security tools (I.e., NGFW, SWG, DLP, WAF) and provides a different, but necessary, function. Pentesting finds exploitable vulnerabilities and unintentional data exposure in hosts, endpoints, applications, web applications, and APIs – functions these tools do not do.
The results of a pen test are compiled into a report and then used to configure security device settings (e.g., WAFs, NGFW) before pen tests are run again to verify the appropriate (re)configurations. Based on the report, this last step is key and provides the best insight regarding the effectiveness of the deployed security tools at stopping common vulnerabilities like SQL injections, brute force attacks, APTs and more. As a result, IT Security leaders typically understand:
- What and where they should ‘fix’ systems first, based on business risk and priorities;
- if they have the correct security tools in place, and
- if these tools are configured properly to stop data breaches, lateral threat movement, and more.
ll of this information helps establish and strengthen an organization’s overall security posture.
IT SECURITY MANAGER
NETWORK ADMINISTRATOR
CYBERSECURITY ANALYST
IT MANAGER
SECURITY OPERATIONS LEAD
CHIEF INFORMATION SECURITY OFFICER