Dynamic Application Security Testing (DAST)
Validated results. Enterprise scale. AI Advisory.
The human layer to our service that ensures accurate vulnerability risk, minimizing of false positives, and prioritized fixes with proven exploits.
Today’s enterprises deploy a wide range of Layer 7 services with APIs and microservices beginning to replace many web applications across the enterprise space. These applications are under a regime of frequent change, and security testing of such systems in terms of security posture is of vital importance. The Edgescan DAST solution provides full stack coverage of your entire application attack surface, with validated and proven vulnerabilities delivered to you as often as you need. We align your scanning frequency to your remediation program to ensure effective and efficient use of the most accurate DAST solution on the market.
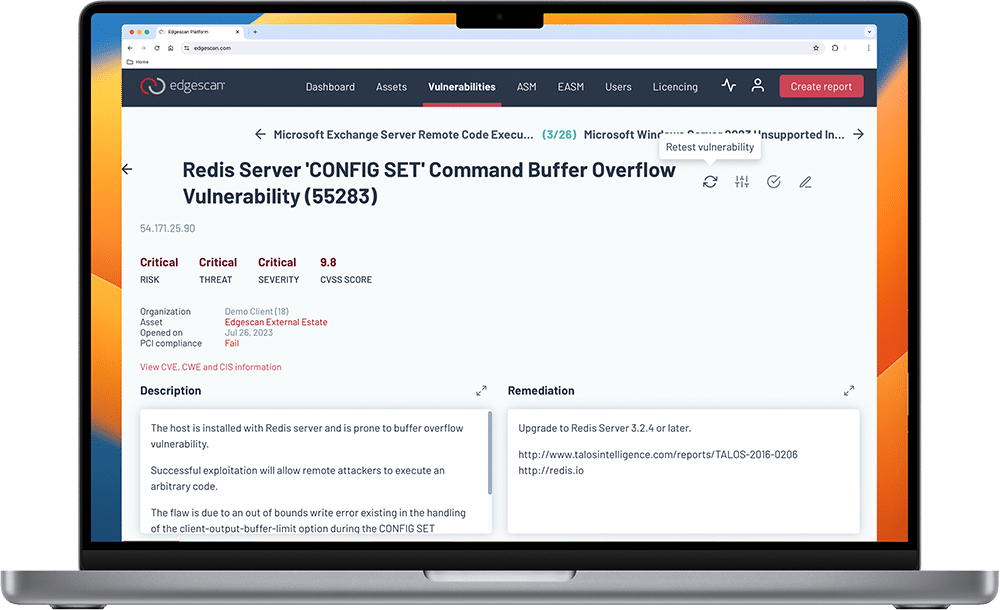
From one application to 10,000, every web application assessed gets the “full-stack” treatment, meaning the application undergoes penetration testing and automated vulnerability assessment. Each and every exposure that is discovered is assessed for severity and whether it is listed as a vulnerability currently being exploited on the public Internet. It’s validated to determine if it is exploitable and a real risk. This makes prioritization much easier.
Each vulnerability is verified by our team of certified experts to ensure that only REAL threats are escalated. Edgescan customers never experience false positives or false alarms.
Validated vulnerability scanning on demand and on a schedule, as often as you need it
Complete visibility to expose weaknesses and risk across your deployed application and web services
Edgescan relays verified vulnerability data into the existing CI/CD toolset, so DevOps teams have the critical data they need earlier in the software development lifecycle.
Organizations spend 25% of their time managing security alerts
Benefits of Dynamic Application Security Testing
Hybrid approach
to assessments
Integrates with
existing tools
Edgescan provides verified vulnerability data into your existing CI/CD tool stack so developers and operations teams have the critical data they need earlier in the software development lifecycle.
The platform seamlessly integrates alerts and notifications with your installed third-party systems for complete visibility across your tool stack.
Customizable reporting
Unlimited and on-demand vulnerability assessments and retesting
Retest as often as needed to verify mitigation at no additional cost – providing peace of mind.
Edgescan Dynamic Application Security Testing (DAST) is a software as a service, sold as an annual subscription.
Contact us for more information on how Edgescan can help secure your business.
IT MANAGER
IT SECURITY MANAGER
NETWORK ADMINISTRATOR
CYBERSECURITY ANALYST
IT MANAGER
SECURITY OPERATIONS LEAD
CHIEF INFORMATION SECURITY OFFICER