This blog post will address recent RCE vulnerability discovered by Edgescan Senior Information Security Consultant, Guram Javakhishvili. These vulnerabilities were discovered while validating alerts as part of Edgescan’s human intelligence verification. These discoveries are shared with clients so they can evaluate and mitigate the risks. The vendor is also notified so they can resolve the issues and improve the overall security of the application.
Concrete5-8.5.2
Concrete5 CMS is an open source powerful content management system. A point and click, free CMS that creates websites. Concrete5 is used by major brands around the world, such as; GlobalSign, U.S.Army, REC, BASF, and many more, see full list here.
Concrete5 is designed for ease of use, for users with a minimum of technical skills. It enables users to edit site content directly from the page.
- Issue: concrete5-8.5.2 Remote Code Execution – Reverse Shell
- Software: concrete5 https://www.concrete5.org/
- Vulnerability: Remote Code Execution – Reverse Shell
- Vulnerable component: File Manager
- Vulnerability disclosed at: https://hackerone.com/reports/768322
- Vulnerable version: 8.5.2
- Stable Fixed release: 8.5.4
Remote Code Evaluation (Execution) is a type of application weakness that can be exploited when user input is injected into a file or a String and evaluated by the language’s parser.
A Remote Code Evaluation is a very serious vulnerability as it is usually easy to exploit and grants full access to an attacker immediately after being exploited. RCE can lead to a full compromise of the susceptible web application and also the web server that it is hosted on.
It is important to note that not only PHP language but almost every programming language has code evaluation functions. While there are sites that allow you to run PHP code on demand, they severely limit what you can do and most importantly they thoroughly check your PHP code to eliminate execution of any dangerous functions with high risk, for example: exec, shell_exec.
If your application is required to allow PHP extension at least do not pass any user-controlled input (content of the file) inside evaluation functions or callbacks. That includes not letting users decide the name and extensions of files that they wish to upload or create in the web application.
During the assessment of the Concrete5’s version 8.5.2, it was noted that it was possible to modify site configuration to upload the PHP file and execute arbitrary commands.
By default, file types such as PHP, HTML and other dangerous file extensions are not allowed, but it was possible to include PHP extension in the legal file list and then upload the file:
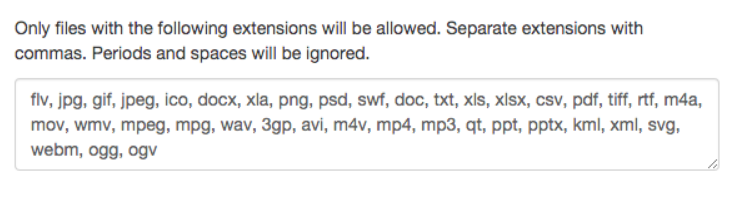
The attacker needs the appropriate permissions (Admin role) in order to edit and allow other file types (file extension).
If the file type such as PHP is added then the user will be able to upload potentially malicious PHP code and execute system commands.
A code for the file upload function is located here at \concrete\controllers\backend\file.php which uses handleUpload() upload file and ConcretePermissions() function to check the permitted file extensions, if the file does not exist in the allowed file type list then the exception will be thrown.
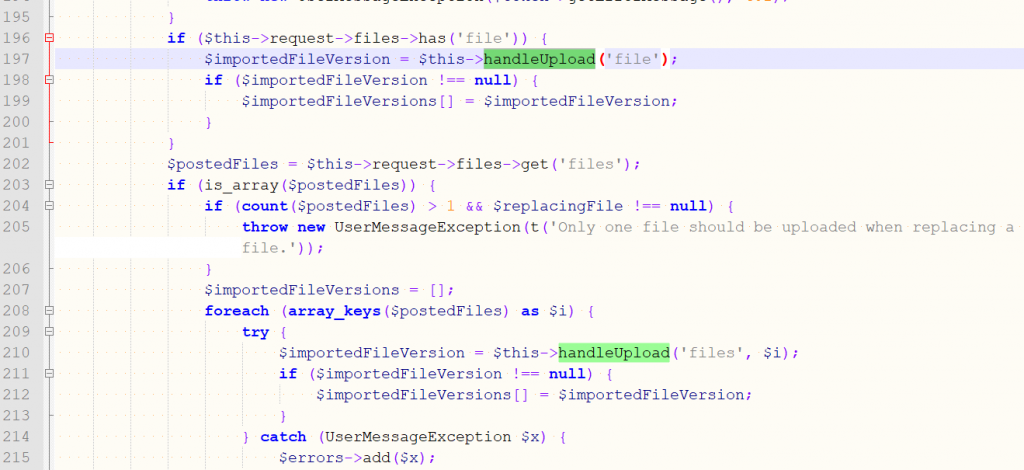
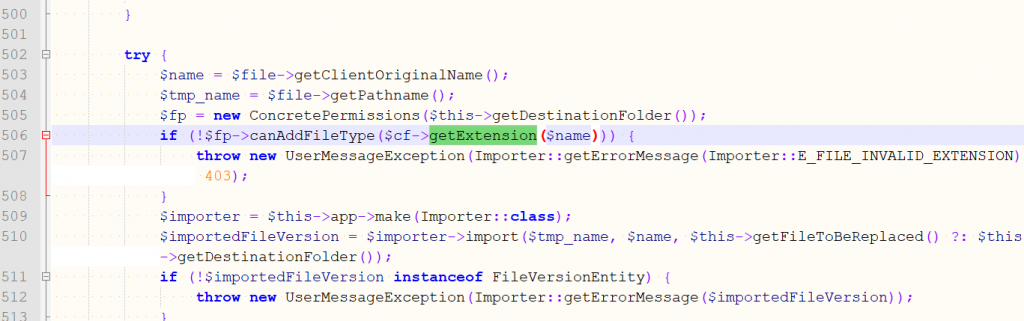
Steps to Reproduce Detailed HERE.
Impact
Reverse shell is a mechanism that allow attacker to have the server shell by exploiting the web server to trigger a connection back. The attacker would be able to take full control over the web server (system).By executing arbitrary commands on the server, an attacker could compromise the integrity, availability and confidentiality. And pivot onto other servers on the internal network.
How to Prevent Remote Code Evaluation
File Upload Forms are a major security threat. If your application is required to allow PHP extension at least do not pass any user-controlled input (content of the file) inside evaluation functions or callbacks. That includes not letting users decide the name and extensions of files that they wish to upload or create in the web application. Sanitizing user input is also an option, but this would not be a best solution as it is most of the time not possible due to the number of possible bypasses of restrictions. In this particular case malicious PHP code is injected into a php file or a String and executed (evaluated) by the PHP parser.
Also, you can lock down your interpreter by changing server configuration, if you could limit interpreter functionality to the minimum required for the application to prevent escalation to system command injections. For example, if your application does not use PHP system() function, you can disable that function in your php.ini file by specifying it in the disable_functions directive. Most common list of dangerous functions that you can disable for PHP are: exec(), passthru(), shell_exec(), system(), proc_open(), popen(), curl_exec(), curl_multi_exec(), parse_ini_file(), and show_source().
- This bug has already been addressed by Concrete5 and the stable fixed release is out already, version: 8.5.4
- Crucially important to keep your installed scripts and CMS platforms up to date. Create a regular schedule to update or patch your CMS, and all installed plugins and themes. Ensure all components are up-to-date.
- At a minimum weekly update is equally important. Regularly backup the CMS and its underlying database.
- Subscribe to a regularly-updated list of vulnerabilities for the specific CMS being used.
- Avoid use of default usernames (e.g., ‘admin’) enforce strong password policy for your CMS’s admin area and server to protect them from the brute force attacks.
- Use a plugin for strong authentication, or two-factor authentication (2FA) for an additional layer of protection.
“A Remote Code Evaluation can lead to a full compromise of the vulnerable web application and also web server. Nearly 2% of vulnerabilities across the fullstack were attributed to RCE in the Edgescan 2020 Vulnerability Stats Report.
At Edgescan, we’re proud of the part we play in identifying vulnerabilities in web apps, alerting vendors and supporting them in making their products as secure as possible. “ Eoin Keary, CEO, Edgescan.
Subscribe to the Edgescan blog to receive updates.
Guram Javakhishvili
Senior Information Security Consultant
Edgescan






