The NIS2 Directive is a comprehensive legislation designed to enhance the EU’s cybersecurity framework significantly. Its main goal is to strengthen the cybersecurity defences of critical infrastructure and essential services reliant on network and information systems. Building on the lessons from the original NIS Directive (2016), NIS2 broadens its focus to confront modern cyber threats and tackle emerging challenges. It specifically addresses the rapid advancements in cloud computing, supply chain security, and digital services, ensuring a more resilient and secure digital environment across the EU.
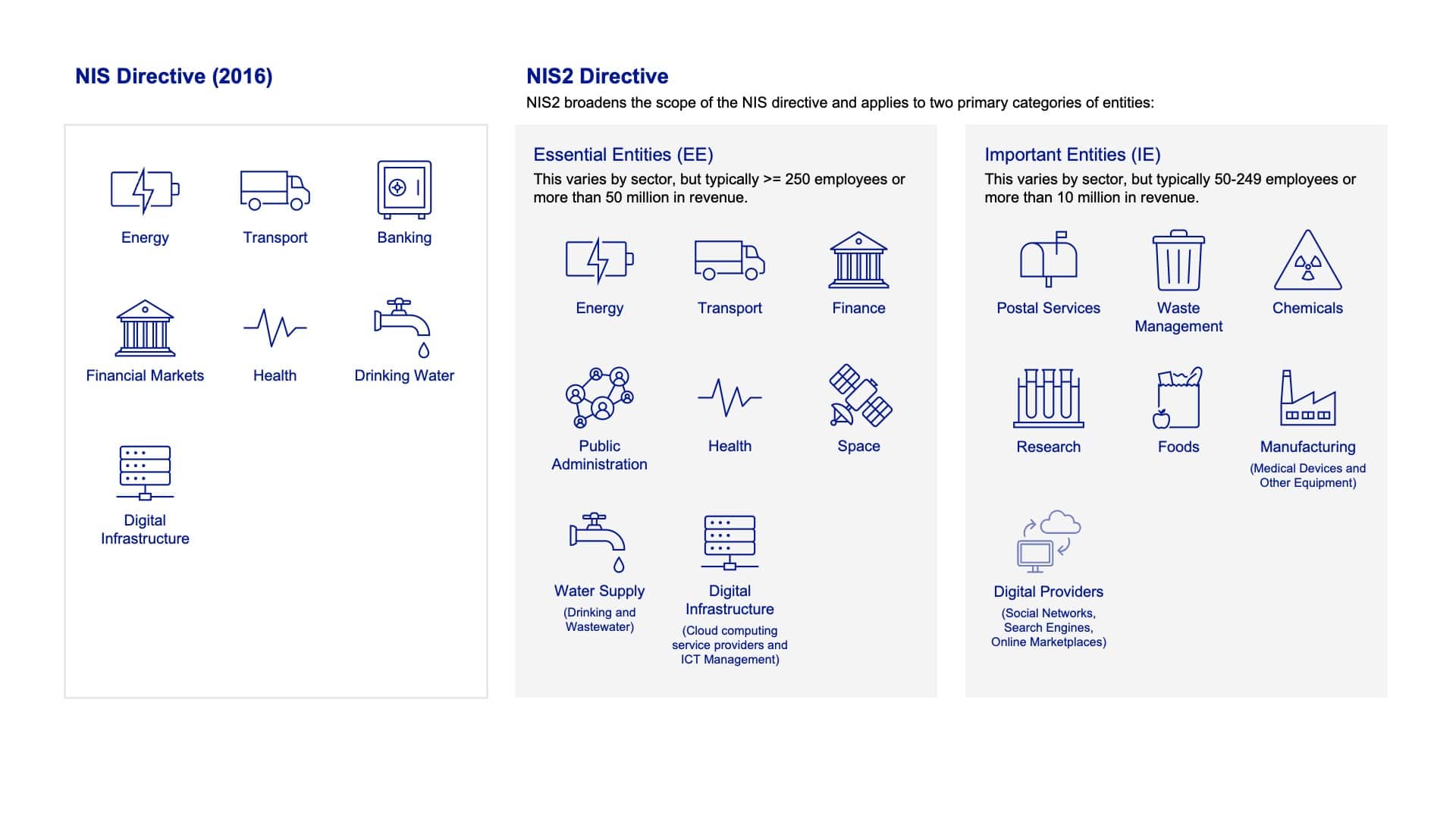
Where Does NIS2 Apply?
NIS2 not only expands within existing sectors (e.g., adding insurance companies to financial services, expanding energy to include district heating and cooling) but also introduces entirely new sectors like postal services, waste management, and food production etc.
Here’s a breakdown of the sectors affected by the original NIS Directive compared to those included in NIS2, and the changes that have been introduced:
What are the Requirements?
What Needs to Be Done to Comply with NIS2?
To strengthen Europe’s defences against cyber threats, the NIS2 Directive introduces new obligations in four key areas: risk management, business continuity, reporting obligations and corporate accountability.
Risk Management: Organizations must enforce robust measures such as incident response plans, supply chain security, network protection, stronger access control, and encryption to combat cyber threats.
Business Continuity: Entities are required to ensure operational resilience, with plans for system recovery, crisis response, and emergency procedures during cyber incidents.
Reporting Obligations: Essential and important entities must report major security incidents swiftly, including a mandatory 24-hour “early warning” for significant events.
Corporate Accountability: NIS2 holds senior management directly accountable for cybersecurity, with penalties and personal liability for non-compliance.
10 Baseline Security Measures
In addition to the four key areas detailed above, NIS2 also mandates the implementation of 10 minimum security measures essential and important entities to counter common cyber threats:
- Conduct risk assessments and establish security policies for information systems.
- Implement policies to evaluate the effectiveness of security measures.
- Use cryptography and encryption where relevant.
- Create a plan for managing security incidents.
- Secure procurement, development, and operation of systems, including vulnerability handling.
- Provide cybersecurity training and ensure basic computer hygiene.
- Establish strict data access controls and track asset usage.
- Ensure up-to-date backups and maintain system access during incidents.
- Utilize multi-factor authentication, encryption for communications, and continuous authentication.
- Strengthen supply chain security by assessing supplier vulnerabilities and adopting appropriate security measures.
How Can Edgescan Help with NIS2 Compliance?
Edgescan, a leading provider of full-stack vulnerability management and penetration testing solutions, is perfectly positioned to assist organizations in achieving NIS2 compliance. Here’s how:
1. Continuous Vulnerability Assessment: Edgescan provides continuous vulnerability scanning and assessment across both network infrastructure and application layers. This aligns with NIS2’s requirement for organizations to regularly assess and mitigate risks.
2. Risk-Based Prioritization: One of the key elements of NIS2 is risk management. Edgescan delivers a risk-based approach to vulnerability management by prioritizing vulnerabilities based on criticality, exploitability, and the business impact they might have.
3. Full-Stack Security: From web applications to network infrastructure, Edgescan covers the entire IT environment, providing a comprehensive overview of all potential attack surfaces. This is crucial for NIS2 compliance, which requires organizations to ensure the security of both their digital and physical systems.
4. Expert-Led Penetration Testing: Edgescan offers hybrid vulnerability management and expert-led penetration testing services, helping organizations uncover hidden vulnerabilities that automated scans might miss. This ensures a thorough assessment and meets the higher security standards demanded by NIS2.
5. Compliance & Reporting Tools: Edgescan provides detailed reports that can assist organizations in demonstrating compliance with NIS2 during audits. These reports are essential for tracking progress, risk mitigation actions.